Hetzner AntiDDoS
Today, large-scale DDoS attacks — are one of the most common ways to negatively impact a website or an entire infrastructure. An attacker sends thousands or millions of fake requests, overloading the bandwidth and server resources. As a result, real users cannot open the site or constantly experience connection problems.
We provide services based on Hetzner (dedicated servers, auction servers, Cloud VPS). Each of these services includes DDoS protection by default (already included in the price). It automatically monitors suspicious traffic, blocks attacks, and protects websites and servers from overload — all at no extra cost to our customers.
What is a DDoS attack
DDoS (Distributed Denial of Service) — is a distributed attack aimed at causing a denial of service.
- Your service receives a huge number of requests not from a single computer, but from entire networks of infected servers and other devices (botnets).
- The network and server resources become occupied by junk traffic.
- In this scenario, requests from real users are processed with huge delays or never reach the server at all.
The attacker’s goal is simple — to make your website or service unavailable.
How Hetzner DDoS protection works
The Anti-DDoS system is deployed within the data center network and implemented on professional Arbor and Juniper hardware. Traffic is analyzed continuously.
Data transmission under normal conditions
Under normal circumstances, traffic from users passes directly through the network equipment to your servers.
All requests are processed as usual, without additional filtering or delays.
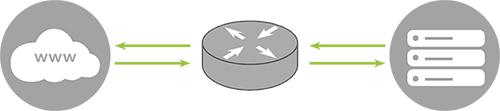
(In the diagram: green arrows between the internet, router, and servers represent clean traffic.)
Data transmission during an attack
When the system detects an anomaly (a spike in traffic volume, packet rate, or suspicious traffic patterns), the protection mechanism is activated:
- All incoming traffic is redirected through filtering nodes (scrubbing centers).
- Junk traffic is detected and discarded.
- Only legitimate requests from real users reach the server.
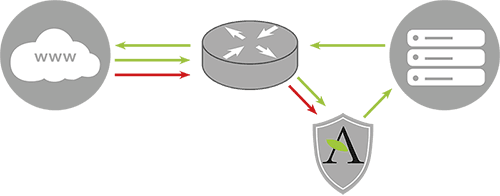
(In the diagram: part of the traffic is marked in red and diverted to the Anti-DDoS shield, while the green traffic continues to the server.)
Filtering stages and methods
1. Automatic detection of attack type
The system reacts not only to raw numbers (traffic volume and packet rate) but also to the nature of the traffic itself.
For example:
- a powerful UDP stream of hundreds of thousands of packets per second is often harmless for a well-configured server,
- while the same volume of SYN packets can lead to a denial of service.
The Anti-DDoS system distinguishes such scenarios and responds to them differently by choosing the appropriate type of filtering.
2. Blocking known attack patterns
Some attacks have well-known patterns. For them, predefined filters and a traffic scrubbing system are used.
The system effectively handles, in particular, the following types of attacks:
- DNS reflection
- NTP reflection
- UDP floods on port 80/UDP
Such traffic streams are detected and blocked before they ever reach the server.
3. Challenge-response and dynamic filters
At the final stage, more "subtle" protection mechanisms are activated:
- filtering SYN floods and DNS floods,
- discarding incorrect and clearly fake packets,
- a flexible response to non-standard attacks.
The system maintains a high level of automation: every new incident is analyzed, and the set of filters and rules is continuously refined and expanded by Hetzner specialists.
How this affects customers
- Protection enabled by default
No hidden fees or surcharges — Anti-DDoS is already included in our Hetzner-based plans (dedicated servers, auction servers, and Cloud VPS). - Constant monitoring
Traffic is analyzed around the clock. As more statistics are collected, the system becomes even better at recognizing attacks. - Minimal impact on legitimate traffic
In normal mode, traffic goes directly to the servers. During attacks, only the malicious portion of the traffic is filtered, so regular users often do not even notice that an attack is in progress. - Protection for more than just websites
Web applications, APIs, game and corporate servers, as well as any other infrastructure, are also protected.
Source: https://www.hetzner.com/unternehmen/ddos-schutz
Hetzner dedicated servers: https://spacecore.pro/dedicated-servers/
Hetzner auction servers (free setup): https://spacecore.pro/dedicated-servers-no-install/
Hetzner Cloud VPS: https://spacecore.pro/hetzner-cloud/








